Bypass Command Prompt Disabled Windows
Introduction
Have you ever faced this message before and given up on executing commands via Command Prompt?

The restriction is often seen in environments such as kiosks PCs and prevents an interactive command prompt with the goal of reducing the possibilities of an attacker.
This post explains how the restriction may be bypassed to obtain (interactive) command execution via Command Prompt to increase the possibilities in a penetration test. Mitigations against these bypasses can be found at the end of the post.
The restriction can be set using the “Prevent access to the command prompt” policy in “User Configuration > Administrative Templates > System”:
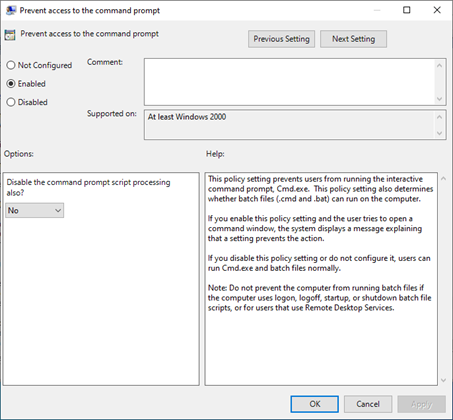
Or setting one of these registry keys (the above policy sets the HKCU one):
HKLM\SOFTWARE\Policies\Microsoft\Windows\System
HKCU\SOFTWARE\Policies\Microsoft\Windows\System
The registry key has the REG_DWORD “DisableCMD” which can have the values:
- 0 = Policy disable
- 1 = Policy enable, disable script processing
- 2 = Policy enable, enable script processing
If the target system is configured with disable script processing (value = 1) in HKLM, then there’s no bypass as far as I know, unless you have administrator privileges that allows changing the HKLM value to 0.
The PowerShell bypass
Firstly PowerShell may not be restricted, if PowerShell is an acceptable alternative, try one of these:
1. Execute “C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe”
2. Execute “C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe”
3. If application allowlisting (e.g. AppLocker) blocks the above paths, you may copy the executables to another path and execute them from there.
The HKCU bypass
This bypass can be used if the registry value is set only in HKCU, the bypass is simply to disable the restriction by setting the value to 0.
The “/k” or “/c” bypass
This bypass can be used if the policy is configured with enable script processing (value = 2 either in HKCU or HKLM).
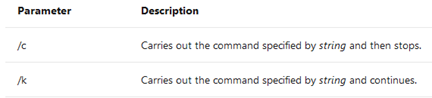
The simplest bypass is to use the “/k” or “/c” parameters of cmd.exe:
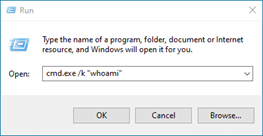
Let’s say we want to run the command “whoami”, this can be done with “Run” prompt:

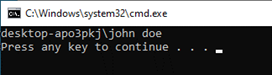
In case of “/k”, the “whoami” command is run, then the Command Prompt “continues” and will thereafter be blocked by the interactive restriction:

In case of “/c” a “pause” command is used to prevent the Command Prompt from closing before we get to see the output:
The AutoRun bypass
Looking into the “/d” parameter of cmd.exe I found that value of the REG_SZ “AutoRun” in “SOFTWARE\Microsoft\Command Processor” will be executed upon start of cmd.exe – first HKLM is executed and then HKCU:

Here is the result of the above when executing “cmd.exe” (with no parameters):
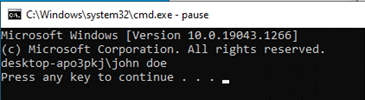
Alternatively, omit the “&& pause” from the registry value and execute “cmd.exe /k” to see the output before Command Prompt closes.
Bypassing “Run” restrictions via shortcut
Environments with a Command Prompt restriction often have all sorts of restrictions in place, such as the “Run” prompt being disabled or preventing arbitrary paths from being accessed via Explorer’s address bar.
These restrictions and their bypasses are many so I will only cover one, what I call the “shortcut” bypass:
1. Create (or edit an existing) shortcut (.LNK) file.

2. Set target to: C:\Windows\System32\cmd.exe /k “whoami”
a. Tip: Use %COMSPEC% or %CMDCMDLINE% to refer directly to cmd.exe path of the system.
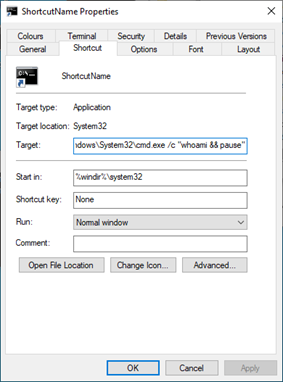
3. Open the shortcut.
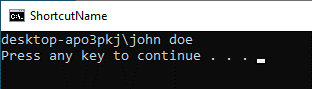
Interactive bypass via batch file
They’re all fun bypasses, but let’s wind back to the policy which stated “This policy settings prevents users from running the interactive command prompt, Cmd.exe”
So far, we’re not really bypassing the interactive part of the policy, and it sucks to edit a shortcut target before running each new command.
One solution create an .BAT or .CMD file, add the below code, and execute it:
@echo off:loopset /p var=command: %var%goto loop
The result is an “interactive” Command Prompt. The batch script saves user input in the variable var, executes it, and starts over:

Interactive bypass via cmd.exe
Performing a “fileless” interactive bypass can also be done, one way is by executing the following:
cmd.exe /q /v:on /k "FOR /L %N IN () DO (set /p var=command: && !var!)"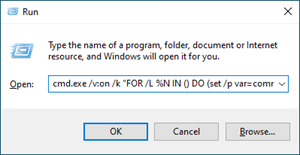
Obviously, if the “Run” prompt is disabled you can add the command in the previously described Bypassing “Run” restrictions via shortcut.
The “/q” parameter is used to turn echo off and make the terminal prettier.
The “/v:on” parameter is used because we’re using FOR instead of the previous GOTO, and thereby also require delayed environment variable expansion – variable expansion now happens at execution time instead of at input time. without it the variable set by the user input won’t be expanded.
You can either use “/c” or “/k”, both have the same behaviour since the loop never stops.
The “FOR /L…” part will start a loop that again saves user input in the variable var, executes it, and starts over.
Mitigations
Methods of preventing the above bypasses do exist:
- The best mitigation against the malicious use of cmd.exe and powershell.exe is to utilize application allow listing using e.g. AppLocker or Windows Defender Application Control.
- The second best mitigation against the cmd.exe bypasses is by disabling command prompt script processing either via Group Policy in the Computer policy or setting the HKLM key “SOFTWARE\Policies\Microsoft\Windows\System” value “DisableCMD” to 1. Make sure to configure it as a Computer Policy or set the HKLM registry key, else the policy can be bypassed as described.
- Prevent execution of other script engines, e.g. powershell.exe and powershell_ise.exe – e.g. with AppLocker or Windows Defender Application Control.
Disabling command prompt script processing also prevents logon, logoff, startup, and shutdown scripts, therefore you may do the following to reduce the risk of bypasses:
- Prevent and/or monitor changes in “SOFTWARE\Microsoft\Command Processor” in both HKCU and HKLM.
- Enable command line auditing (see https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/manage/component-updates/command-line-process-auditing and https://nxlog.co/documentation/nxlog-user-guide/windows-command-line-auditing.html)
- Enable PowerShell logging (see https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging_windows?view=powershell-7.1 and https://nxlog.co/documentation/nxlog-user-guide/powershell-activity.html)
- Associate .BAT and .CMD files with e.g. Notepad so that they won’t execute, and ensure that file type associations cannot be modified.
- Prevent usage of the “Run” prompt and other ways of executing cmd.exe – after configuring these you should prevent the described bypasses by:
- Prevent creation of shortcuts (.LNK files) via right-click.
- Prevent modification of all existing shortcuts.
- Use File Screening Management[2] to prevent creation of shortcuts on network shares.
[1] https://ss64.com/nt/cmd.html
[2] https://docs.microsoft.com/en-us/windows-server/storage/fsrm/file-screening-management
