F5 Security Advisory CVE-2022-1388 Update
Summary
F5 has issued a security advisory warning about a flaw that may allow unauthenticated attackers with network access to execute arbitrary system commands, perform file actions, and disable services on BIG-IP. The vulnerability is tracked as CVE-2022-1388 and has a CVSS v3 severity rating of 9.8, categorized as critical. Its exploitation can potentially lead up to a complete system takeover. According to F5’s security advisory, the flaw lies in the iControl REST component and allows a malicious actor to send undisclosed requests to bypass the iControl REST authentication in BIG-IP. F5 has also provided a month round-up of all patches which should be applied for the month of May 2022 – https://support.f5.com/csp/article/K55879220
Advisory Details
Date: May 4th 2022
Update: May 18th 2022
Risk: Critical
Priority: Critical
Action: Administrators should review all edge F5 appliances and ensure the latest patches have been applied based on the chart below. Three effective mitigations that may be used temporarily for those who can’t apply the security updates immediately.
- Block all access to the iControl REST interface of your BIG-IP system through self IP addresses
- restrict access only to trusted users and devices via the management interface
- modify the BIG-IP httpd configuration.
The following source of these is at Greynoise where you can integrate the feed with your firewall
Integration Feed
- https://api.greynoise.io/v3/tags/04778d66-600a-4c60-83d0-e734800e6868/ips?format=txt
Indicators of Compromise (IOC):
- https://viz.greynoise.io/tag/f5-big-ip-crawler
128.90.59.158
213.227.154.147
23.237.66.142
45.142.122.34
103.144.149.142
103.169.216.25
160.16.87.84
185.212.61.84
188.165.87.96
188.165.87.99
188.165.87.103
221.124.246.102
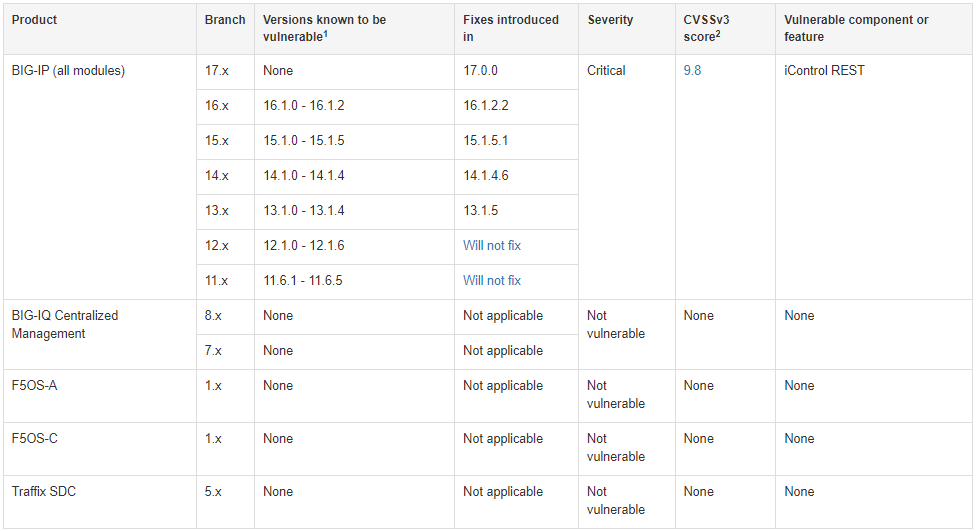
Affected Products:
- BIG-IP versions 16.1.0 to 16.1.2
- BIG-IP versions 15.1.0 to 15.1.5
- BIG-IP versions 14.1.0 to 14.1.4
- BIG-IP versions 13.1.0 to 13.1.4
- BIG-IP versions 12.1.0 to 12.1.6
- BIG-IP versions 11.6.1 to 11.6.5
Fix Version
- BIG-IP versions v17.0.0
- BIG-IP versions v16.1.2.2
- BIG-IP versions v15.1.5.1
- BIG-IP versions v14.1.4.6
- BIG-IP versions v13.1.5.
Older Version 12.x and 11.x will not receive a fixing patch.
Mitigation
Until it is possible to install a fixed version, you can use the following sections as temporary mitigations. These mitigations restrict access to iControl REST to only trusted networks or devices, thereby limiting the attack surface.
- Block iControl REST access through the self IP address
- Block iControl REST access through the management interface
- Modify the BIG-IP httpd configuration
Block iControl REST access through the self IP address
You can block all access to the iControl REST interface of your BIG-IP system through self IP addresses. To do so, you can change the Port Lockdown setting to Allow None for each self IP address in the system. If you must open any ports, you should use the Allow Custom option, taking care to disallow access to iControl REST. By default, iControl REST listens on TCP port 443 or TCP port 8443 on single NIC BIG-IP VE instances. If you modified the default port, ensure that you disallow access to the alternate port you configured.
Detection
I have observed the URL pattern below actively being targeted “/mgmnt/tm/util/bash” coming from many IP addresses known to IBM Threat Exchange as Scanning and Botnet based on reputation. This is a stern reminder this is being actively targeted by malicious actors and highly suggest patching or mitigation any threat exposure your organization may have.
F5 has also released a bash script which can be used for testing the exploit and additional github repository has POC for testing purposes only
https://github.com/0xf4n9x/CVE-2022-1388
Snort Threat Rules
alert tcp any any -> any $HTTP_PORTS (msg:”BIG-IP F5 iControl:HTTP POST URI ‘/mgmt./tm/util/bash’ and content data ‘command’ and ‘utilCmdArgs’:CVE-2022-1388”; sid:1; rev:1; flow:established,to_server; flowbits:isnotset,bigip20221388.tagged; content:”POST”; http_method; content:”/mgmt/tm/util/bash”; http_uri; content:”command”; http_client_body; content:”utilCmdArgs”; http_client_body; flowbits:set,bigip20221388.tagged; tag:session,10,packets; reference:cve-2022-1388; reference:url,github.com/alt3kx/CVE-2022-1388_PoC; priority:2; metadata:service http;)
Suricate Emerging Threat Rules
SID 2036546
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET EXPLOIT F5 BIG-IP iControl REST Authentication Bypass (CVE 2022-1388) M1"; flow:established,to_server; content:"POST"; http_method; content:"/mgmt/tm/util/bash"; http_uri; fast_pattern; content:"Authorization|3a 20|Basic YWRtaW46"; http_header; content:"command"; http_client_body; content:"run"; http_client_body; distance:0; content:"utilCmdArgs"; http_client_body; distance:0; http_connection; content:"x-F5-Auth-Token"; nocase; http_header_names; content:!"Referer"; content:"X-F5-Auth-Token"; flowbits:set,ET.F5AuthBypass; reference:cve,2022-1388; classtype:trojan-activity; sid:2036546; rev:2; metadata:attack_target Web_Server, created_at 2022_05_09, deployment Perimeter, deployment SSLDecrypt, former_category EXPLOIT, performance_impact Low, signature_severity Major, updated_at 2022_05_09;
SID 2036547
alert http $HOME_NET any -> any any (msg:"ET EXPLOIT F5 BIG-IP iControl REST Authentication Bypass Server Response (CVE 2022-1388)"; flow:established,to_client; flowbits:isset,ET.F5AuthBypass; content:"200"; http_stat_code; file_data; content:"kind"; content:"tm|3a|util|3a|bash|3a|runstate"; fast_pattern; distance:0; content:"command"; distance:0; content:"run"; distance:0; content:"utilCmdArgs"; distance:0; content:"commandResult"; distance:0; reference:cve,2022-1388; classtype:trojan-activity; sid:2036547; rev:1; metadata:attack_target Web_Server, created_at 2022_05_09, deployment Perimeter, deployment SSLDecrypt, former_category EXPLOIT, performance_impact Low, signature_severity Major, updated_at 2022_05_09;)
References
https://www.cisa.gov/uscert/ncas/alerts/aa22-138a
https://support.f5.com/csp/article/K23605346
